Join the Level Discord — connect with IT professionals, share ideas, and get real-time updates
Check it outProduct
Discover the best RMM software for internal IT teams and small businesses in 2025. Compare features, pricing, automation tools, and integrations to find the right solution for your IT operations.

If you are running an internal IT department or managing a small business, keeping systems efficient, secure, and well maintained can be a constant challenge. Tasks like device maintenance, patch scheduling, software deployment, and remote troubleshooting consume valuable time without the right IT automation tools, especially when supporting a distributed workforce or multiple office locations.
This is where modern it management software becomes essential. Instead of juggling disconnected tools, IT teams can centralize monitoring, automation, and support within a single platform designed to scale with business needs.
In this comparison guide, you will learn how remote monitoring and management works, which features matter most, how to evaluate platforms, and which solutions stand out in 2025. You will also see how it management software helps reduce manual workload while improving security and uptime.
RMM software is a category of it management software that enables IT professionals to monitor, manage, and maintain devices, networks, and infrastructure from a central dashboard. These platforms collect real time data, generate system health alerts, and allow remote troubleshooting of endpoints.
For internal IT teams, this means full visibility and control across all devices with faster response times and proactive support. For small businesses, it management software reduces operational costs by automating maintenance tasks and minimizing downtime.
Key capabilities typically include:
Modern platforms provide secure remote access for Windows, macOS, Linux, and sometimes mobile devices. This allows technicians to resolve issues quickly without interrupting users. Reliable remote access is a core requirement of effective it management software.
Automated patching is critical for security and compliance. Leading platforms apply operating system and third party updates on schedule, ensuring vulnerabilities are addressed without disrupting productivity.
Real time monitoring detects issues early by tracking CPU usage, memory health, disk capacity, and network performance. Proactive alerts help teams prevent outages before users are impacted.
Advanced platforms support automation workflows for tasks like software deployment, system cleanup, and service restarts. Automation improves consistency and allows IT staff to focus on higher value work, which is one of the biggest benefits of modern it management software.
A complete asset inventory tracks hardware specs, installed software, warranties, and policies. This supports budgeting, audits, and long term planning across the organization.
Look for platforms that integrate with helpdesk tools, PSA systems, network monitoring solutions, and security software. Seamless integration eliminates manual data entry and improves operational efficiency.
Strong security features include encryption, multi factor authentication, role based access, and compliance reporting. High quality it management software supports regulatory requirements and internal governance standards.
Level is a cloud based it management software platform that is simple to deploy and easy to use. It offers browser based access, real time monitoring, automation scripts, patch scheduling, and secure peer to peer remote access.
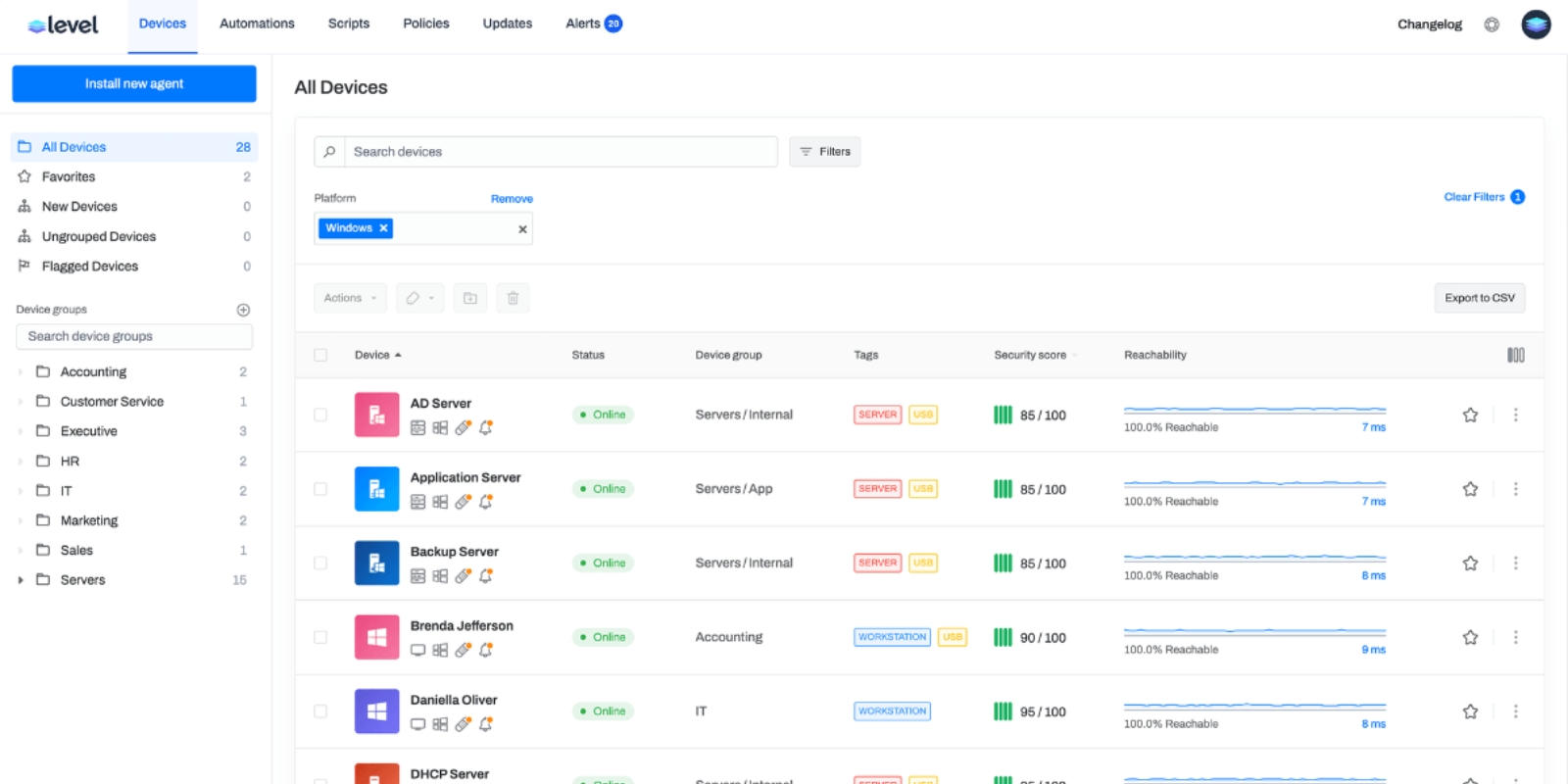
Key features:
Pricing: $2 per endpoint per month
Best for: Businesses looking for low cost remote IT management solutions for startups that still provide enterprise grade features.
N-sight is an all in one platform that supports managed service provider MSP needs as well as internal IT departments.

Key features:
Best for: IT teams that want a complete IT management software suite with automation and monitoring capabilities.
NinjaOne is known for ease of use and proactive IT support capabilities.
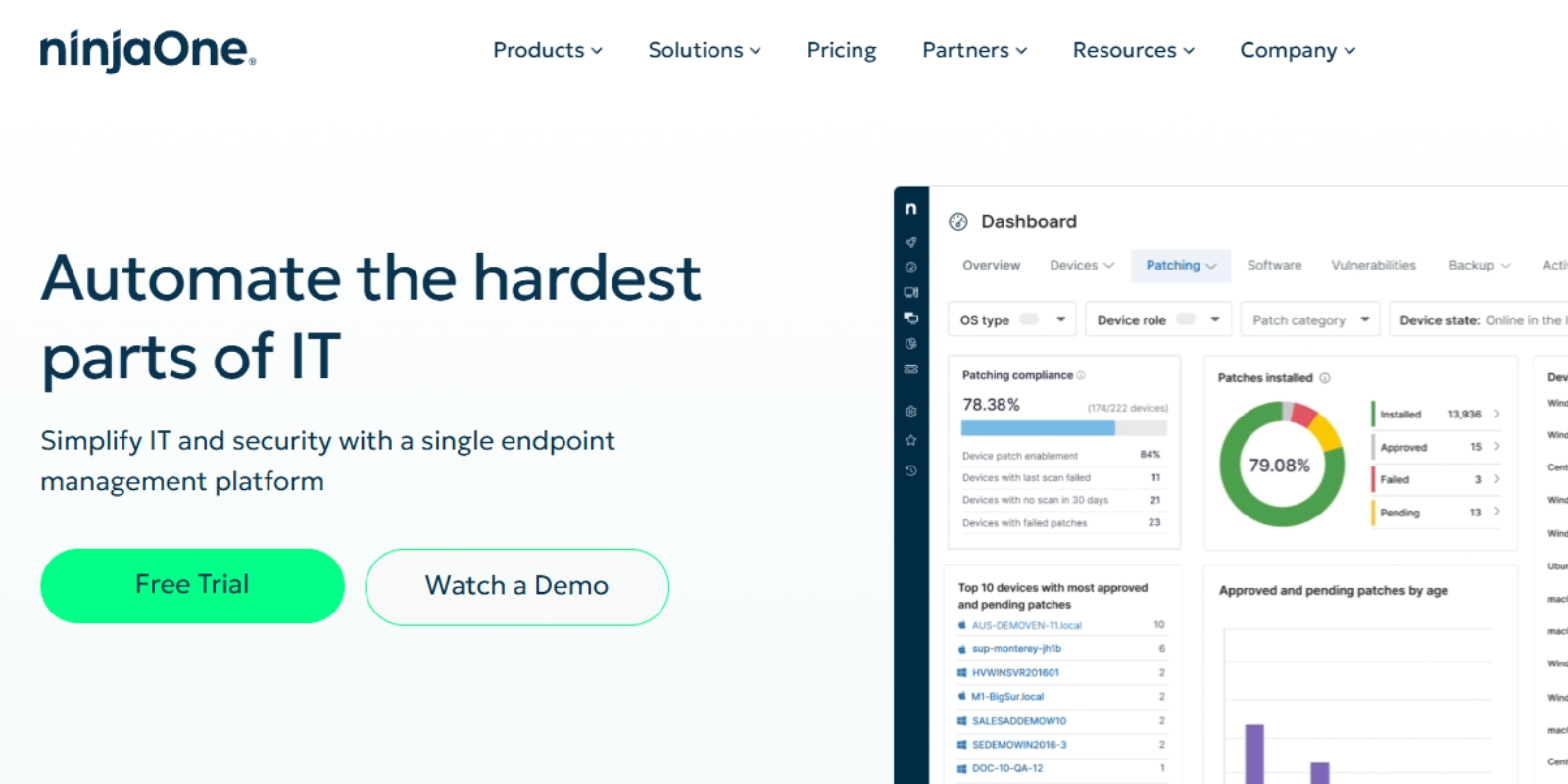
Key features:
Best for: SMBs looking for easy to use RMM for small businesses that can scale quickly.
Atera combines RMM, PSA, and AI driven automation in one subscription.
Key features:
Best for: Businesses with a high number of endpoints but smaller IT teams.
Datto RMM delivers enterprise grade remote support with advanced automation capabilities.
Key features:
Best for: Mid size to large businesses with complex IT environments.
ConnectWise Automate is built for advanced customization and scripting.
Key features:
Best for: IT teams needing RMM tools for managing multiple endpoints with tailored automation.
LogMeIn Resolve is a browser based RMM that focuses on security and endpoint visibility.
Key features:
Best for: Businesses managing hybrid or fully remote teams.
When selecting it management software, match features to your operational needs. Small teams may prioritize ease of use and affordability, while larger teams often require advanced monitoring and automation.
Consider scalability, pricing models, security controls, and integration capabilities. Always test platforms through free trials to confirm they fit your workflows.
What is the best option for internal IT teams?
The best it management software depends on your environment, device count, and automation needs. Platforms like Level, NinjaOne, and ConnectWise Automate are commonly selected for scalability and scripting.
Can small businesses use these platforms without dedicated IT staff?
Yes. Many solutions are designed to be beginner friendly and include guided automation and intuitive interfaces.
Is cloud based deployment better than on premise?
Cloud based platforms are easier to maintain and scale, while on premise deployments may offer deeper customization.
Is this type of software secure?
Most platforms include encryption, access controls, and compliance features, but security capabilities should always be validated before purchase.
The right it management software allows IT teams to work proactively, automate repetitive tasks, and maintain strong security standards. Whether you need advanced monitoring, automation, or a cost effective starting point, there is a solution that fits your business and scales with growth.
At Level, we understand the modern challenges faced by IT professionals. That's why we've crafted a robust, browser-based Remote Monitoring and Management (RMM) platform that's as flexible as it is secure. Whether your team operates on Windows, Mac, or Linux, Level equips you with the tools to manage, monitor, and control your company's devices seamlessly from anywhere.
Ready to revolutionize how your IT team works? Experience the power of managing a thousand devices as effortlessly as one. Start with Level today—sign up for a free trial or book a demo to see Level in action.